What is Role-Based Access Control? Explained
Role-Based Access Control is a vital security approach that ensures only authorized individuals can access specific resources, particularly important in the venture capital sector for protecting sensitive information.
Role-Based Access Control
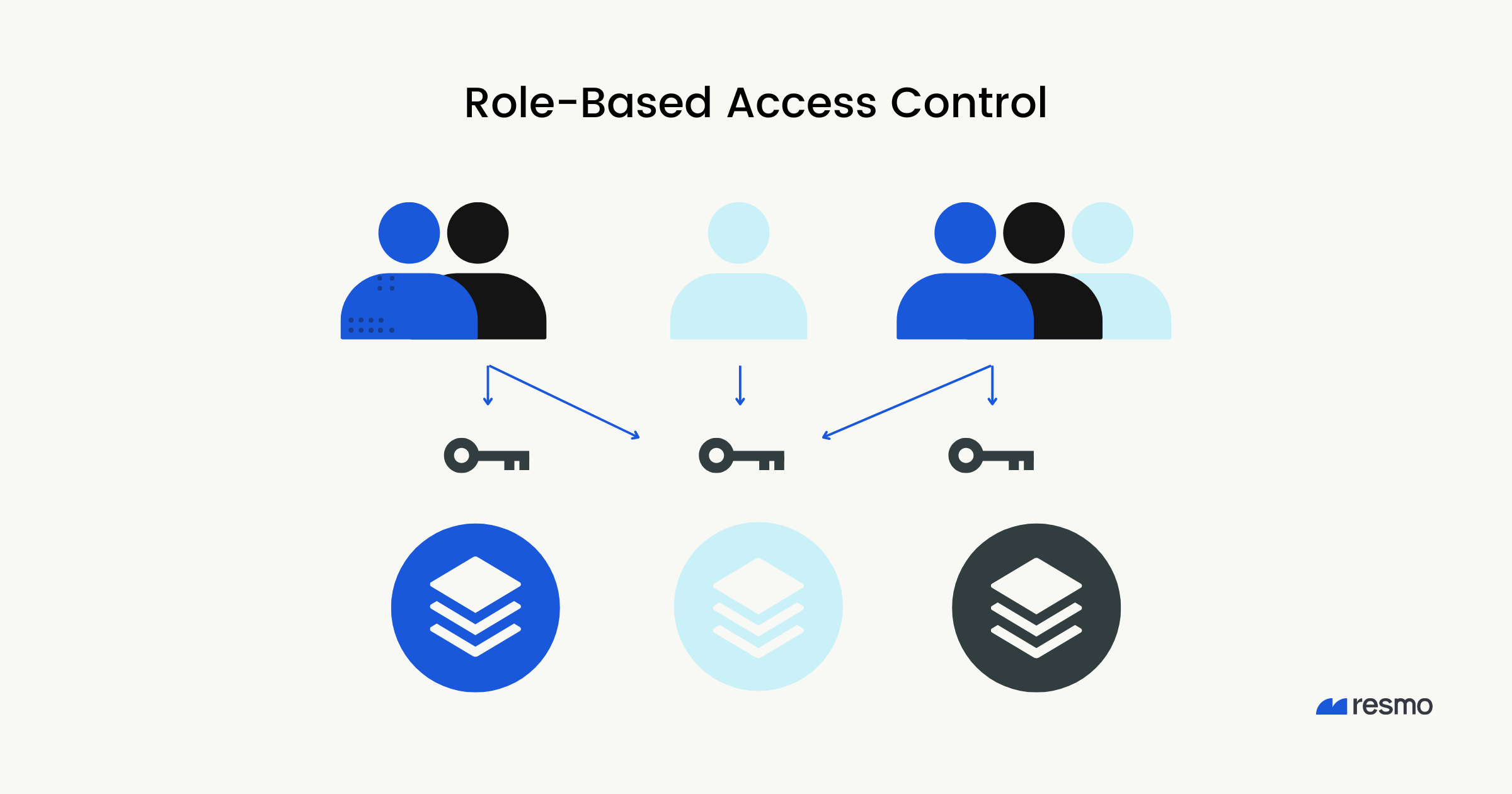
Role-Based Access Control, or RBAC, is a crucial aspect of security in today's digital landscape. I mean, have you ever wondered how companies manage who gets to see what information? That's where RBAC comes into play. It's all about defining what tasks people can do and what resources they can access based on their roles in an organization.
What is Role-Based Access Control?
At its core, RBAC restricts network access based on a user's role within the company. For example, an intern doesn't need access to sensitive data like financial reports, but a financial analyst does. This model keeps data safe while ensuring that employees can do their jobs without unnecessary roadblocks. Trust me, balancing access is tricky but incredibly important.
How Role-Based Access Control Works in VC
In the venture capital (VC) world, the stakes are high. Confidentiality is everything. Imagine a startup founder sharing sensitive information with investors. RBAC ensures that only those who need to know have access. So, analysts might get access to certain documents while partners have access to everything. This not only protects the information but also creates trust among all parties involved.
Benefits of Role-Based Access Control for Venture Capital
Implementing RBAC in VC brings multiple advantages. First, it boosts security. By limiting access based on roles, you effectively reduce the risk of data breaches. I remember working with a startup that had a relaxed approach to access control, and they learned the hard way why it matters. Second, it streamlines operations. Employees can focus on their roles without worrying about whether they can access the necessary data.
Implementing Role-Based Access Control in Your Organization
Ready to dive in? Here’s how you can start implementing RBAC:
- Define Roles: Start by identifying the different roles in your organization. After all, you can't assign access if you don't know who does what.
- Assign Permissions: Next, attach the specific permissions needed for each role. Think about what each role truly needs to function effectively.
- Create Rules: Set clear rules on how these roles interact. For instance, a manager should have different permissions than a junior employee.
- Employ Tools: There are great software solutions designed to make RBAC easy. These tools can automate much of the work for you.
- Audit Regularly: Finally, don’t forget to audit permissions regularly. It’s essential to ensure that as roles change, access does too.
To get a deeper look into this, check out this insightful article on TechTarget.
Role-Based Access Control Challenges and Solutions
Like any system, RBAC has its challenges. One common issue is the potential for overly complex rules that can confuse employees. There’s also the risk of roles becoming outdated. To tackle these problems, keep your role definitions clear and simple. Also, regularly update the access rights as job functions evolve in your organization.
Wrap-Up: The Future of Role-Based Access Control in VC
As the digital landscape continues to evolve, RBAC will remain a cornerstone of secure access management. For organizations, embracing RBAC isn't just about preventing unauthorized access. It's about creating a culture of trust, transparency, and security.
For those curious about the technical side, check out this video by IBM Technology that compares Role-based access control with Attribute-based control.
In conclusion, now you know the importance of Role-Based Access Control. It's not just a security measure; it's a strategic approach that every organization should consider seriously.
